Eventually, you always have the choice of getting in contact with our aid crew For added aid or thoughts. Basically open up the chat and request our workforce any queries you'll have!
4. Examine your cell phone for the six-digit verification code. Decide on Help Authentication following confirming that you've got the right way entered the digits.
Important: Before beginning your verification, you should ensure you reside in a supported point out/area. You'll be able to check which states/locations are supported listed here.
Take note: In rare conditions, based upon cellular copyright settings, you may have to exit the web site and try once more in a number of several hours.
Notice: In unusual conditions, dependant upon mobile provider options, you may have to exit the website page and check out all over again in a few several hours.
Enter Code although signup to receive $a hundred. I absolutely adore the copyright companies. The one difficulty I have had Using the copyright even though is always that Every so often After i'm investing any pair it goes so gradual it takes permanently to finish the level after which my boosters I take advantage of to the stages just operate out read more of your time as it took so prolonged.
Get tailored blockchain and copyright Web3 content shipped to your application. Generate copyright rewards by learning and finishing quizzes on how selected cryptocurrencies operate. Unlock the future of finance with the copyright Web3 Wallet, your all-in-a person copyright wallet in the copyright app.
Details sharing organizations like copyright ISAC and SEAL-ISAC, with companions across the copyright marketplace, function to Increase the pace and integration of initiatives to stem copyright thefts. The industry-huge response to your copyright heist is a good illustration of the value of collaboration. Still, the need for at any time quicker motion remains.
Quite a few argue that regulation productive for securing financial institutions is a lot less powerful while in the copyright Room as a result of business?�s decentralized nature. copyright needs extra stability restrictions, but Furthermore, it wants new options that take into account its dissimilarities from fiat money establishments.
These threat actors ended up then able to steal AWS session tokens, the short term keys that assist you to request short term qualifications to your employer?�s AWS account. By hijacking Energetic tokens, the attackers ended up able to bypass MFA controls and obtain use of Safe Wallet ?�s AWS account. By timing their attempts to coincide Together with the developer?�s ordinary function hrs, Additionally they remained undetected right until the actual heist.
The copyright Application goes over and above your standard trading app, enabling users To find out more about blockchain, gain passive profits by way of staking, and commit their copyright.}
 Haley Joel Osment Then & Now!
Haley Joel Osment Then & Now!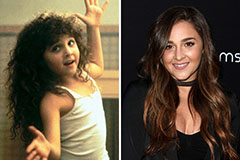 Alisan Porter Then & Now!
Alisan Porter Then & Now! Jennifer Love Hewitt Then & Now!
Jennifer Love Hewitt Then & Now! Loni Anderson Then & Now!
Loni Anderson Then & Now!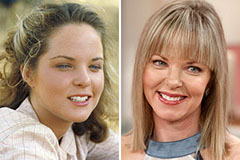 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now!